download 1 wget https://gi thub.com/kubernetes/ dashboard/blob/m aster/aio/ deploy/recommended/ kubernetes-dashboard.yaml
modfiy images 修改为微软镜像1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 vim kubernetes-dashboard.yaml kind: Deployment ... spec: containers: - name: kubernetes-dashboard image: gcr.azk8s.cn/google_containers/kubernetes-dashboard-amd64:v1.10.1 kind: Service ... spec: type: NodePort ports: - port: 443 targetPort: 8443 nodePort: 30001
kubectl apply 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 [root@node1 ~]# kubectl apply -f kubernetes-dashboard.yaml [root@node1 ~]# kubectl get pods -n kube-system | grep dashboard kubernetes-dashboard-7dddd6dcc4-cdndp 1/1 Running 0 3m6s [root@node1 ~]# kubectl describe svc kubernetes-dashboard -n kube-system Name: kubernetes-dashboard Namespace: kube-system Labels: k8s-app =kubernetes-dashboard Annotations: <none> Selector: k8s-app =kubernetes-dashboard Type: NodePort IP: 10.233.56.85 Port: <unset> 443/TCP TargetPort: 8443/TCP NodePort: <unset> 30001/TCP Endpoints: 10.233.92.28:8443 Session Affinity: None External Traffic Policy: Cluster Events: <none> [root@node1 ~]# kubectl get service -n kube-system -o wide NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR coredns ClusterIP 10.233.0.3 <none> 53/UDP,53/TCP,9153/TCP 24h k8s-app =kube-dns kubernetes-dashboard NodePort 10.233.56.85 <none> 443:30001/TCP 4m54s k8s-app =kubernetes-dashboar
create admin-user 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 vim admin-user.yaml apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: admin namespace: kube-system --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: admin namespace: kube-system
get token 1 2 3 4 [root@node1 ~]# kubectl describe serviceaccount admin -n kube-system [root@node1 ~]# kubectl get secret -n kube-system | grep admin-token admin-token-f2zrn kubernetes.io/service-account-token 3 3m57s
token info 1 2 [root@node1 ~]# kubectl -n kube-system get secret admin-token-f2zrn -o jsonpath={.data.token} | base64 -d eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1mMnpybiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImEwOTQ1OTAyLTkyNDQtMTFlOS05OGIxLTAwMGMyOTAzMjQ0MCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.kpQSZtTActGYAiVtQI7lMKJdSaXDY4UBtOJJuU1uMLWcL6uzz99XntTBo3kPWCmzGv4lk_5bbCX747TOme2R2PGLAsXr8XYppQkl7vjrqRmWwv2ag29X8mfDF3JeYmI0YEsAlDxUaGJoBKGoGVJafxXPLVeTpVZkbLK1OcMumFEYi488q2FCUF7agQOoYTTmaWO7Z5IRxJBTSkZlOh_pfIwbDaKK3Y5xcETCHv25BqeX1Gks-LbqYNvegkLj0sF479hEMwfhVPLc_HA-BkAXkMEsSmLXjMu1Xz7Oodg2GPIaGpVLPtPd7QYlQTFyB1apb31ibaFJ8gLdOFNEaRuZqQ
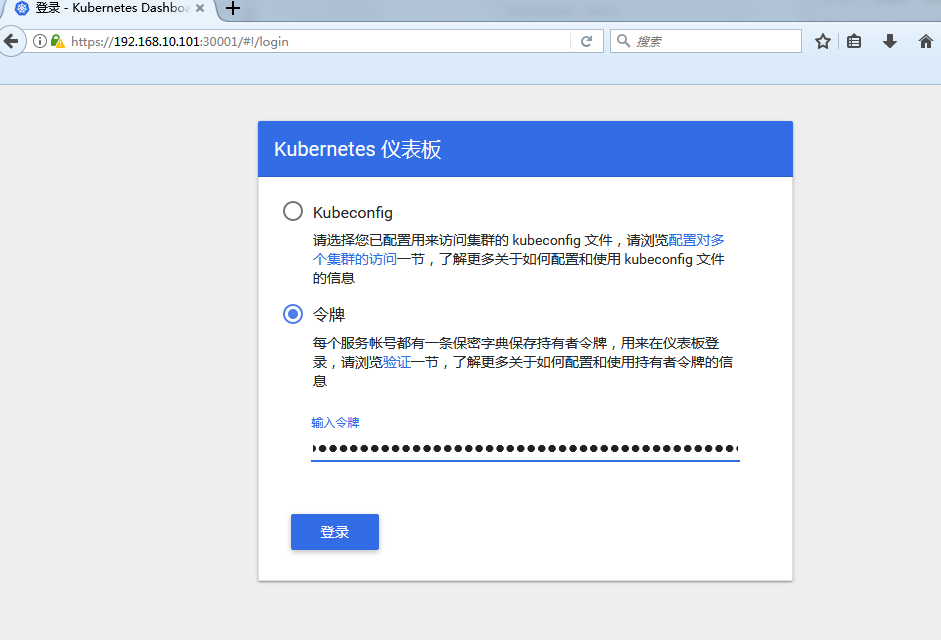
复制token
access url https://192.168.10.101:3001
upgrade certificate kubernetes dashboard 默认配置是一张空证书,浏览器访问时会一直提示非安全连接,访问时需要添加例外,谷歌浏览器新版本无法登陆。
创建自签名CA 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 [root@node1 tls]# cd /etc/kubernetes/ssl [root@node1 tls]# mkdir tls && cd tls #生成私钥 [root@node1 tls]# openssl genrsa -out ca.key 2048 Generating RSA private key, 2048 bit long modulus ..............+++ ...................+++ e is 65537 (0x10001 ) #生成自签名证书 [root@node1 tls]# openssl req -new -x509 -key ca.key -out ca.crt -days 3650 -subj "/C=CN/ST=GD/L=GZ/O=IT/OU=OPS/CN=CA" #查看CA内容 [root@node1 tls]# openssl x509 -in ca.crt -noout -text
签发dashboard证书 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 [root@node1 tls]# openssl genrsa -out dashboard.key 2048 Generating RSA private key, 2048 bit long modulus .......+++ ......................................................+++ e is 65537 (0x10001 ) #申请签名请求 [root@node1 tls]# openssl req -new -sha256 -key dashboard.key -out dashboard.csr -subj "/C=CN/ST=GD/L=GZ/O=IT/OU=OPS/CN=192.168.10.101" vim dashboard.cnf extensions = san [san] keyUsage = digitalSignature extendedKeyUsage = clientAuth,serverAuth subjectKeyIdentifier = hash authorityKeyIdentifier = keyid,issuer subjectAltName = IP:192.168 .10 .101 ,IP:127.0 .0 .1 ,DNS:192.168 .10 .101 ,DNS:localhost #签发证书 [root@node1 tls]# openssl x509 -req -sha256 -days 3650 -in dashboard.csr -out dashboard.crt -CA ca.crt -CAkey ca.key -CAcreateserial -extfile dashboard.cnf Signature ok subject=/C=CN/ST=GD/L=GZ/O=IT/OU=OPS/CN=192.168 .10 .101 Getting CA Private Key #查看证书 [root@node1 tls]# openssl x509 -in dashboard.crt -noout -text ...
挂载dashboard证书 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 [root@node1 ~]# kubectl delete -f kubernetes-dashboard.yaml secret "kubernetes-dashboard-certs" deleted secret "kubernetes-dashboard-csrf" deleted serviceaccount "kubernetes-dashboard" deleted role.rbac.authorization.k8s.io "kubernetes-dashboard-minimal" deleted rolebinding.rbac.authorization.k8s.io "kubernetes-dashboard-minimal" deleted deployment.apps "kubernetes-dashboard" deleted service "kubernetes-dashboard" deleted [root@node1 ssl]# kubectl create secret generic kubernetes-dashboard-certs --from-file ="tls/dashboard.crt,tls/dashboard.key" -n kube-system secret/kubernetes-dashboard-certs created [root@node1 ssl]# kubectl get secret kubernetes-dashboard-certs -n kube-system -o yaml [root@node1 ~]# kubectl create -f kubernetes-dashboard.yaml secret/kubernetes-dashboard-certs configured secret/kubernetes-dashboard-csrf created serviceaccount/kubernetes-dashboard created role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created deployment.apps/kubernetes-dashboard created service/kubernetes-dashboard created
导出证书 1 2 3 #从服务器中导出证书在客户端安装 [root@node1 tls]# yum install -y lrzsz [root@node1 tls]# sz ca.crt
https://github.com/kubernetes/dashboard/wiki/Certificate-management#public-trusted-certificate-authority